SECURITY POLICY
1. INTRODUCTION TO AGHRMS SECURITY POLICY
With increasingly complex security threats in today’s technology-driven world, an organization’s technology leaders bear the responsibility of securing & protecting customer information, employee data & intellectual property of their company & affiliated subsidiaries. With the proliferation of Cloud Computing, many security concerns are raised.
In Computing, Security comprises Cybersecurity & Physical Security. Both areas are used by organizations to guard against unauthorized access to data centres & other Enterprise Computer Systems. Information Security, which refers to maintaining confidentiality, integrity & availability of data, is a subset of Cybersecurity, which requires consistent, coordinated efforts throughout an Information System, which includes:
- Information Security
- Application Security
- Network Security
- Disaster Recovery / Business Continuity Planning
- Operational Security
- End-user Training & Education
Next, we look into how AGHRMS achieves 100% for each of the above layers.
2. SECURITY OVERVIEW: AGHRMS
2.1 HRMS SERVER ARCHITECTURE

Here’s a Macro-Level Representation of AGHRMS Applications.
AGHRMS primarily utilizes 2 sets of servers:
(a) Web Servers: Customers will be using AGHRMS application modules via one of these sets of web servers, which are running MS IIS as well as AGHRMS HR Solutions Suite.
(b) Database Servers: This is where AGHRMS’s customer data is stored, & runs on MS SQL Server.
2.2 APPLICATION SECURITY
Key Considerations:
- Authentication: All passwords are encrypted with a secret cryptographic key & a cryptographic hash function.
- Authentication Requests: This is performed using a one-way hash to ensure password security.
- Access Control & Authorization: AGHRMS is a role-based system with 3 main roles, namely:
- Employee: Each user can only view or manage his/her own records.
- Manager: Each user can only view or approve or reject requests from his/her own team.
- Administrators: Each user can configure policies, level of access rights & manage transactions.
- Session Management: Users who have been idle for over a certain period of time will be automatically logged out of AGHRMS with a typical timeout period of 20 minutes,configurable at a per customer basis.
- Command Injection Flaws: By default, AGHRMS validates all Data Input Fields for Cross-Site Scripting & Command Injection Attacks.
2.3 INFORMATION SECURITY
Information Security (IS) refers to the confidentiality, integrity, availability & Accessibility of Systems’ Data from external threats & those with malicious intent.
2.3.1 DATA CONFIDENTIALITY
Confidentiality refers to preventing information from being leaked & disclosed to unauthorized parties.

Data Segregation: AGHRMS is a Multiple-Tenant Software-as-a-Service (SaaS) application with 2 ways of hosting:
(a) Shared Hosting: Multiple customers are hosted within the same server, where each customer has a separate portal linked to a separate database instance. This ensures each customer’s data is stored in a separate database, which eliminates possibility of customers accessing other customers’ data.
(b) Dedicated Hosting: Only 1 customer is hosted within 1 server.
2.3.2 INTEGRITY
Integrity: This refers to protecting information from being changed or modified by unauthorized parties. User Access to AGHRMS is protected by the Transport Security Layer (TLS) which secures network traffic from passive eavesdropping, active tampering or message forgery.
2.3.3 AVAILABILITY
Availability: This refers to availability of information to authorized parties only upon request. A user can only access AGHRMS’s portal upon successful authentication & login at any given time.
2.4 NETWORK SECURITY
AGHRMS hosts its’ servers only with top global hosting partners Amazon Web Services & Microsoft Azure Web Servers. To learn more, you can find the Data Centre Certification Compliance in these URLs as follows:
- https://d1.awsstatic.com/whitepapers/Security/AWS_Security_Whitepaper.pdf
- https://azure.microsoft.com/en-us/overview/trusted-cloud/
Server Access Is Tightly Controlled:
- Web Servers: Only HTTPS & HTTP ports are open to public.
- Database Servers: Only SQL connection is accepted from authorized servers.
2.5 BUSINESS CONTINUITY PLANNING
2.5.1 OBJECTIVE
Objective: To document AGHRMS’s processes so that our customers are proficient to operate our systems within minimal to no disruption to their operational tasks.
If a customer’s plan is covered by SLA, please refer to this SLA for targets.
- Recovery Time Objective (RTO) of 8 Hours
- Recovery Time Objective (RPO) of 24 Hours.
2.5.2 BACKUP POLICY
Below is an overview of AGHRMS Backup Policy.
(a) Backup image of the Production Server is done every 24 hours, which are stored in a separate data center from the production servers.
(b) Customers’ database is also backed up & stored in remote locations in each night.
2.5.3 ANNUAL RESTORATION EXERCISE
Our team conducts an Annual Restoration Exercise so that:
- Server Images can be restored
- Database Backups can be restored
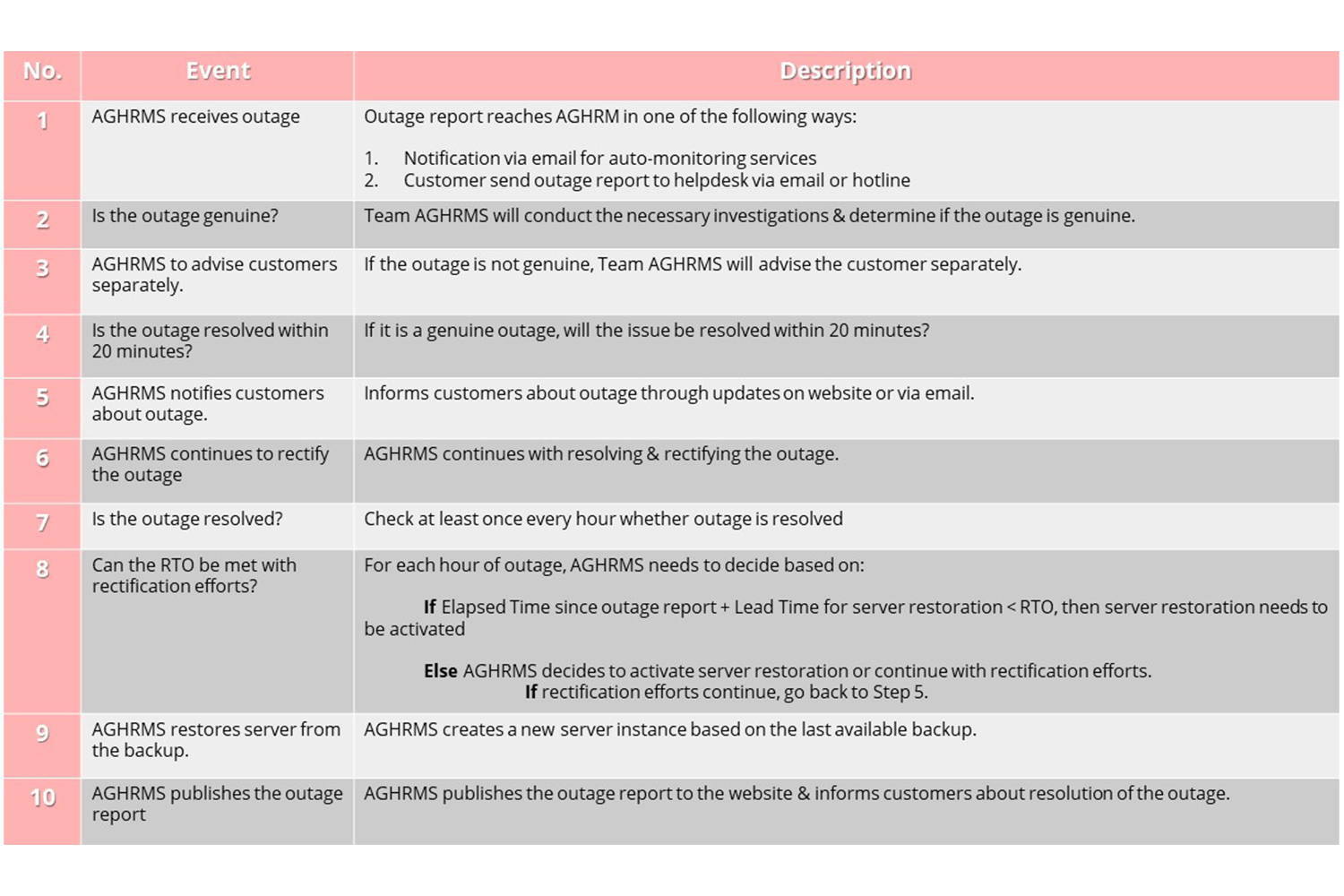
2.5.4 STANDARD PROCEDURE DURING OUTAGE INCIDENT
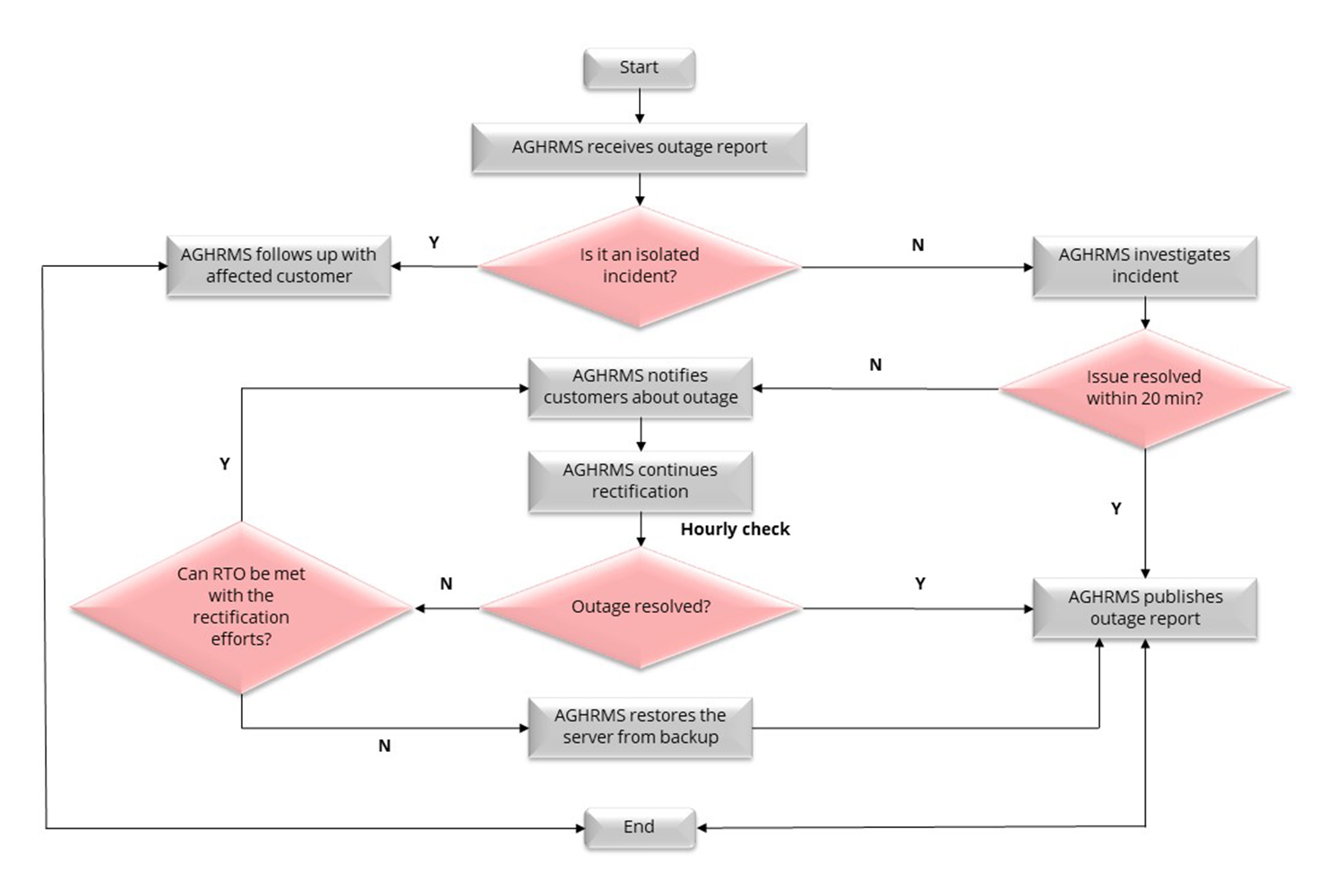
In the event of an outage, here is the course of action to be taken:
2.6 OPERATIONAL SECURITY
To help organizations enforce their IT Security Policy, AGHRMS offers Password Policy Tools for this purpose.
- Password Length: 4 to 14 Characters
- Warning Before Password Expiry: 3 Days
- Available For Configuration.
- Enforce Password History
- Enforce Complex Password
- Configure Password Age (In Days)
- Number of Passwords To Remember: Up To 20 Passwords
